Table of Contents
Many firms are prioritizing mobile efforts these days since research suggests that increased mobility helps businesses enhance their operations and efficiency.
Increases in organizational mobility, on the other hand, usually result in a rise in the number of mobile devices accessing your systems from afar. And for your security staff, this implies an increasing number of endpoints and risks to secure in order to prevent a data breach at your company.
Mobile malware, as in the past, is one of the most common dangers to mobile security. However, as Verizon’s 2020 Mobile Security Index Report demonstrates, there are new hazards that businesses must consider in order to stay safe.
The most common and critical mobile security threats that businesses will encounter in 2021 are listed below.
Table of Contents
4 Different Types of Mobile Security Threats
Most people think of mobile security risks as a single, all-encompassing issue. However, there are four major sorts of mobile security concerns that businesses must be aware of to defend themselves:
- Mobile Application Security Threats: When individuals download apps that appear to be legal but skim data from their device, this is known as an application-based threat. Spyware and malware, for example, steal personal and business information without people recognizing it.
- Web-Based Mobile Security Threats: Web-based hazards are subtle and go undiscovered most of the time. They occur when users browse infected websites that appear to be functioning normally on the surface but, in reality, automatically download harmful content to their devices.
- Mobile Network Security Threats: Cybercriminals can steal unencrypted data while using public WiFi networks, making network-based risks more widespread and dangerous.
- Mobile Device Security Threats: Theft or loss of a device are the most common physical hazards to mobile devices. This threat is especially dangerous for businesses because hackers have direct access to the hardware where confidential data is housed.
The most prevalent examples of these risks are listed here, along with methods that businesses can take to defend themselves.
1. Social Engineering
When unscrupulous actors send bogus emails (phishing attacks) or text messages (smishing attacks) to your employees, they are attempting to deceive them into giving over personal information such as passwords or downloading malware onto their devices.
According to reports from cybersecurity firm Lookout and Verizon, workplace mobile phishing assaults have increased by 37%, and phishing attacks will be the leading source of data breaches globally in 2020.
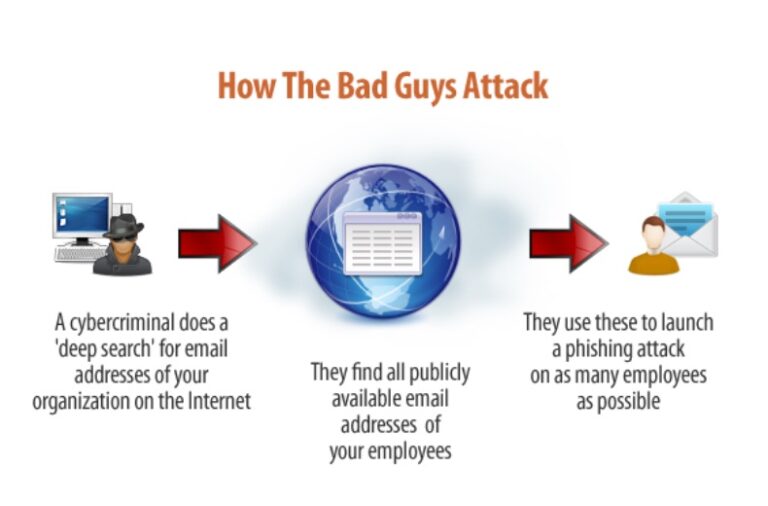
Phishing Attack Countermeasures
The best protection against phishing and other social engineering assaults is to teach employees how to recognise suspicious phishing emails and SMS messages so they don’t fall for them. Reducing the amount of employees with access to sensitive data or systems can also help protect your company from social engineering attacks by reducing the number of ways attackers can obtain access to key systems or information.
2. Data Leakage via Malicious Apps
“Enterprises face a considerably higher threat from the millions of generally available apps on their employees’ devices than from mobile malware,” says Dave Jevans, CEO and CTO of Marble Security.
Because 85 percent of today’s mobile apps are essentially insecure, this is the case. “Today, hackers may easily identify an unprotected mobile app and utilise that unprotected app to create broader attacks or steal data, digital wallets, backend details, and other juicy pieces directly from the app,” according to Tom Tovar, CEO of Appdome.
When your employees go to Google Play or the App Store to download programmes that appear to be harmless, the apps will ask for a list of permissions before they can be downloaded. These permissions typically demand access to files or folders on the mobile device, and most individuals simply scan over the list of permissions and agree without thoroughly evaluating them.
This lack of oversight, on the other hand, might leave devices and businesses susceptible. Even if the software performs as expected, it has the potential to mine corporate data and distribute it to a third party, such as a rival, exposing critical product or business data.
How to Protect Against Data Leakage
Using mobile application management (MAM) tools is the best approach to protect your organisation from data leaks caused by malicious or unprotected applications. These tools allow IT administrators to manage corporate apps on employees’ devices (wipe or modify access permissions) without interfering with their personal apps or data.
3. Unsecured Public WiFi
Because there’s no way of knowing who set up the network, how (or if) it’s secured with encryption, or who’s now accessing or watching it, public WiFi networks are inherently less secure than private networks. Furthermore, as more firms provide remote work choices, the public WiFi networks your employees use to access your servers (for example, from coffee shops or cafés) may pose a security risk to your company.
Cybercriminals, for example, frequently set up WiFi networks that appear legitimate but are actually a front for capturing data that travels through their system (a “man in the middle” attack). Here’s an example of what that looks like:

This isn’t a far-fetched scenario. It’s relatively easy to set up phoney WiFi hotspots in public places with fully legitimate network names, and people are eager to connect, as evidenced by studies conducted at the 2016 Democratic and Republican conventions, as well as an experiment conducted by a Magic researcher in 2019.
How to Reduce Risks Posed By Unsecured Public WiFi
Requiring employees to utilise a VPN to access corporate systems or data is the greatest approach to safeguard your firm from dangers over public WiFi networks. This ensures that their session remains private and safe, even if they access your systems via a public network.
4. End-to-End Encryption Gaps
A hole in an encryption gap is similar to a hole in a water pipe. While the point where the water enters the pipe (your users’ mobile devices) and exits the pipe (your systems) may be secure, the hole in the middle allows bad actors to gain access to the water flow.
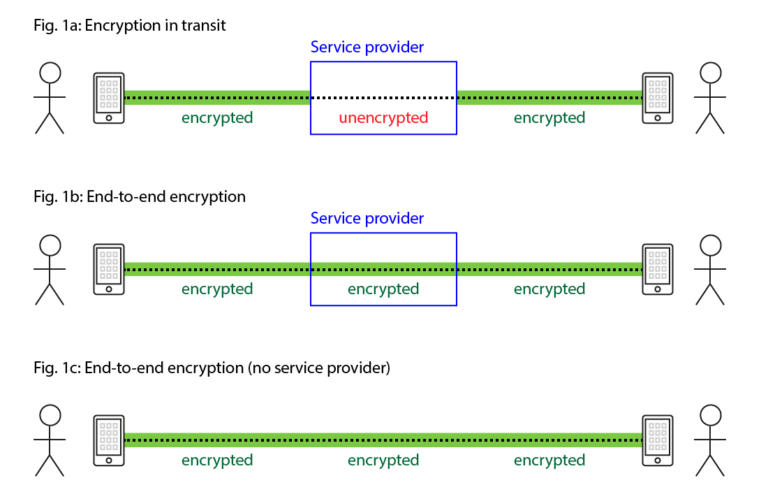
One of the most common examples of an encryption gap is unencrypted public WiFi networks (which is why they pose such a significant risk to businesses). Because the network isn’t secured, fraudsters can gain access to the information your employees share between their devices and your systems.
WiFi networks, however, aren’t the only thing that may be exploited; any application or service that isn’t protected might provide attackers access to important company data. Any unencrypted mobile messaging apps that your employees use to communicate work-related information, for example, could provide an entry point for a bad actor.
Solution: Ensure Everything is Encrypted
End-to-end encryption is required for any sensitive work data. This means ensuring that any service providers you interact with encrypt their services to prevent illegal access, as well as encrypting your users’ devices and systems.
5. Internet of Things (IoT) Devices
Mobile devices that access your company’s systems are expanding beyond smartphones and tablets to include wearable technology (such as the Apple Watch) and physical hardware (like Google Home or Alexa). Bad actors can utilise IP addresses on many of the latest IoT mobile devices to obtain access to your organization’s network through the internet if those devices are connected to your systems.
According to statistics, you probably have more IoT devices connected to your networks than you think. In a research conducted by Infoblox, 78 percent of IT leaders from four countries indicated that over 1,000 shadow IoT devices accessed their networks every day.
How to Combat Shadow IoT Threats
Identity and access management (IAM) systems like Auth0, as well as mobile device management (MDM) tools, can assist you address shadow IoT risks. IoT/Machine-to-Machine (M2M) security, on the other hand, is still in a bit of a “wild west” phase right now. As a result, it is up to each company to put in place the necessary technological and regulatory rules to ensure that their systems are secure.
6. Spyware
Spyware is used to survey or collect data and is most typically installed on a mobile device when consumers click on a malicious advertisement (“malvertisement”) or are tricked into downloading it unintentionally through scams.
Whether your employees use an iOS or Android mobile, these devices are prime targets for spyware data mining, which could include sensitive corporate information if the device is connected to your systems.
How to Protect Against Spyware
Dedicated mobile security software (such as Google’s Play Protect) can assist your staff in detecting and removing malware that may have been installed on their devices and is being used to access company data. Maintaining the most up-to-date operating systems (and software) on your employees’ devices helps safeguard their devices and your data from the latest spyware threats.
7. Poor Password Habits
Organizations whose employees use personal devices to access company networks are vulnerable to these terrible password habits. Because both personal and work accounts may be accessed from the same device using the same password, it makes it easier for a bad actor to break into your networks.
However, because hackers can use weak or stolen credentials to access critical data through enterprise mobile apps, these practises open the door to credential-based brute force cyberattacks like credential stuffing or password spraying.
How to Reduce or Eliminate Mobile Password Threats
The National Institute of Standards and Technology (NIST) Password Guidelines are widely considered as the international standard for password best practises. Following these guidelines—and requiring that your staff do the same—can help you avoid being harmed by passwords that are weak or stolen. Password managers can make it easier for your personnel to adhere to these rules.
Requiring your employees to log in with more than one authentication element (multi-factor authentication, or MFA) reduces the danger of a bad actor gaining access to your systems because they’ll have to validate their identity using additional authentication factors.
Finally, using passwordless authentication can help you completely eliminate password risks. For example, using a facial scan as a primary (or secondary) authentication element could still prevent unwanted access if a mobile device is stolen or accessed illegally.
8. Lost or Stolen Mobile Devices
Devices that are lost or stolen are not a new issue to businesses. However, as more individuals work remotely from public places such as cafes or coffee shops and use a wider range of devices to access your systems, lost and stolen gadgets are becoming a greater threat to your business.
How to Safeguard Your Device Against Loss or Theft
First and foremost, make sure your staff understand what to do if they misplace their equipment. Because most devices come with remote access to erase or move data, it’s a good idea to ask employees if those services are turned on.
Mobile device management (MDM) software can also help you protect, encrypt, or wipe important company data from a lost or stolen smartphone, as long as the software was installed before the device went missing.
9. Out of Date Operating Systems
Mobile security, like other data security projects, necessitates ongoing efforts to identify and fix vulnerabilities that bad actors use to obtain unauthorised access to your systems and data.
Many of these flaws are addressed by operating system updates from companies like Apple and Google. In 2016, Apple, for example, discovered three zero-day vulnerabilities that exposed its devices to spyware attacks and provided a patch to safeguard customers from these flaws.
These fixes, however, will only secure your company if your staff keep their devices updated at all times. According to Verizon’s Mobile Security Index Report, 79 percent of workplace mobile devices have operating system updates left in the hands of employees.
How Do I Update My Mobile Operating System?
Organizations may deliver upgrades to managed Android and iOS devices from both Google and Apple. This functionality is frequently provided by third-party MDM tools (for example, Jamf).
IAM Tools Can Assist in Securing Company Mobile Apps
Organizations can utilize Identity and Access Management (IAM) tools to secure the apps and data that users access from their mobile devices, such as:
- Limiting which devices and users have access to company applications and data, as well as which sections of those apps they can utilize.
- Using security features like multi-factor authentication (MFA), brute force attack prevention, and more, you can track user behavior and secure access in the case that something appears suspicious.

